Mobile application data security and privacy – best practices
With the increasing use of mobile solutions in our daily lives, digital acceleration has also led to increased attacks and fraud in the virtual world, making it an ever more pressing issue.
Mobile applications have become an integral part of our lives for communication, entertainment, financial management, and storing sensitive data like personal information and payment details. As the usage of these applications increases, it becomes crucial to prioritize their security in design and use.
Security is not just a technical issue but also an ethical and legal one. Securing user data is now a key element in building trust and reputation in the world of mobile technology. In case of a security breach, companies not only risk losing data but also suffer reputational damage and legal consequences.
Mobile solutions face multiple threats, such as hacking, data theft, location theft, and malware. Therefore, while designing and launching a mobile application, always remember that security is the foundation upon which the entire mobile ecosystem is built.
Mobile application security basics
To establish a strong foundation for mobile app security, it is essential to implement some fundamental principles. Here are some basic guidelines that can help you protect your app and users' information:
- Data encryption at rest and in transit
Data encryption is the fundamental step in safeguarding sensitive information in mobile apps. Encryption at rest protects the data stored on a user's device from unauthorized access. It is crucial for preventing theft or access to sensitive information.
Encryption in-transit, on the other hand, includes the security of data transmitted between the user's devices and the application server. Without this protection, data is at risk of being intercepted by potential attackers. Encryption protocols such as SSL/TLS are the standard for securing data traffic in mobile applications.
- Secure storage of passwords and credentials
It is vital to secure credentials like passwords to protect users' sensitive data. It's a good idea to use secure password storage practices such as hashing and salting passwords. Hashing turns the password into an irreversible string, meaning that the content is not stored in the database. Salting, on the other hand, adds a unique value (sol) to the password before hashing, which prevents "rainbow table" attacks. It is good practice to store such data on the server and not directly in the application.
- Regular updates and security patches
Mobile apps require constant updates and security patches to remain secure against new threats. App updates introduce new features and include essential security patches. It is crucial to encourage users to regularly update their apps to give them access to the latest security features.
We will analyze the needs of your business
and suggest how you can take care of the security of your mobile application.
Authorization and Authentication
Authorization and authentication are crucial elements in ensuring the security of mobile applications. They enable you to verify that only authorized users have access to the application.
Multi-Factor Authentication Methods:
It is recommended to use multi-factor authentication methods, also known as MFA, in mobile applications. This means that users can use additional security measures like an SMS code or a fingerprint scan, in addition to the traditional password login. The introduction of multiple levels of authentication significantly increases the level of security.
Session and Access Token Management
Sessions and access tokens are essential for managing user access to application resources. Sessions are used to track user activity within the application, while access tokens verify identity when communicating with the server.
Protection against Man-in-the-Middle attacks
These attacks occur when an attacker attempts to intercept communication between the user's device and the application server. Therefore, it is crucial to ensure secure data transmission against attacks.
Protecting against MitM attacks requires the use of appropriate practices and technologies, such as:
- Use of encryption protocols such as SSL/TLS, which support the security of communication between the user and the server.
- Two-factor authentication, which provides an additional layer of security.
- Make your users aware of downloading regular updates to their operating system, browser and also applications.
Implementing effective authorization and authentication methods is a critical element in ensuring user data security and privacy in mobile applications.

Code-Level Security
Code-level security is the foundation for ensuring the durability and resilience of mobile applications against attacks and threats. It includes practices for writing secure code, analyzing and auditing code, and using tools to automatically detect vulnerabilities.
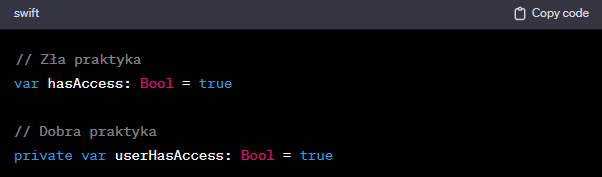
First and foremost, it is critical to focus on writing secure code. The use of precise interchangeable names, data access control, and the use of proven encryption methods become indispensable elements in the application development process. By taking care of every line of code, we build a solid defensive wall for our applications.
Code analysis and auditing is the next step towards code-level security. Regular code reviews are designed to identify potential security vulnerabilities and programming errors. It's also worth using advanced automated code-scanning tools that identify vulnerabilities and allow you to respond quickly to a potential threat.
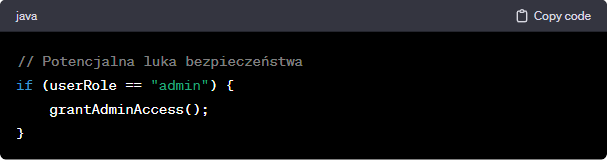
It's also worth using advanced automated code-scanning tools that identify vulnerabilities and allow you to respond quickly to a potential threat. Knowledge of security best practices and current cybersecurity trends is an effective barrier against potential attacks. Regular training allows you to keep the team up to date and effectively counteract possible threats.

As a result, investing in code-level security is a critical step for any mobile application project. A solid foundation not only ensures that the application will last, but also that users will feel comfortable using it without worrying about their privacy. Secure code is a guarantee of stability in today's world, where applications are regularly exposed to attacks.
Using Automatic Vulnerability Detection Tools
In the world of technology, there are many advanced tools available that can scan application code automatically to detect potential vulnerabilities and bugs. These tools use various techniques of static and dynamic analysis to identify vulnerabilities.
There are many tools available for automatic vulnerability detection, including:
- Nessus - a security scanning tool that identifies operating systems, applications, and networks vulnerabilities. It provides automatic scanning and reporting of results.
- Veracode - a SAST (Static Application Security Testing) platform that automatically scans source code for vulnerabilities and security bugs.
- OWASP ON (Zed Attack Proxy) – a tool for testing the security of web applications. It provides automated scanning and vulnerability analysis capabilities, including SQL injection, Cross–Site Scripting, and Cross-Site Request Forgery (CSRF) vulnerabilities.
We understand the importance of code-level mobile application security. Addressing it at every stage of application development helps avoid many potential threats and maintains user confidence.
Application security testing
Security testing is a crucial process in mobile software development aimed at identifying potential threats and vulnerabilities before they are exploited by attackers. This process includes penetration testing, security test automation, and bug reporting programs.
Penetration testing and its role in ensuring security
Penetration testing, also known as ethical hacking, involves a controlled attempt to attack an application to identify weaknesses and vulnerabilities. Security experts carry out these tests by using different attack methods. This type of testing helps identify potential vulnerabilities and enables programmers to fix bugs before attackers exploit them.
Automation of security tests
Automation of security tests is an approach that uses tools and scripts to run tests on the application. This includes source code scanning, network traffic analysis, and attack simulation. Automation enables fast and efficient application security testing, especially for applications that are large in scope and complex in structure.
User-level security
Application security involves protecting the user interface and its relationships. Security at the interface level is crucial to shield users from social engineering attacks and provide them with a sense of confidentiality and safety. Protection from phishing and other social engineering attacks.
Phishing is a common tactic used by attackers to obtain confidential information from users by posing as a trustworthy source. To prevent this, mobile applications should include anti-phishing mechanisms, such as warnings about suspicious links or login pages that appear to be inauthentic.
In practice, protecting against phishing in mobile applications is a critical aspect of ensuring user safety. Implementing mechanisms to warn users of suspicious links or fake login pages is crucial. Here are some examples of how such a mechanism might work in practice:
- Reporting of suspicious cases - Users can report phishing cases directly from the application. This interactive approach allows for dynamic database updates and creates a safe user environment.
- Cybersecurity training - Applications can provide users with brief training on how to identify potential phishing threats. Educating users is an essential prevention element and can reduce the risk of responding to false requests.
Implementing these mechanisms not only increases the security level of mobile applications but also educates users about the potential threats associated with phishing, creating a cybersecurity-aware user.
Secure alerts and notifications for users
Secure alerts and notifications for users are essential in mobile applications. Notifications and messages should not be misleading or abused. Avoid bombarding users with messages and ensure reliable content.
Privacy by Design
Privacy by Design is an approach that prioritizes the protection of user data from the beginning of the application development process. It means incorporating security and privacy practices into the design of the user interface. The "private by default" principle should be used, meaning that the application should automatically protect the privacy of users, and they should be able to adjust their privacy settings according to their preferences.
UI-level security ensures users feel secure and confident in mobile applications. With the right precautions and security-focused design, apps can protect users from a variety of threats and keep their data private.
Data storage and processing
Data security is a crucial aspect of mobile applications, particularly when sensitive user information is involved. There are several key issues related to data storage and processing in mobile apps that should be considered:
Best practices for data storage
Storing data in mobile apps requires a careful approach to security. However, there are best practices that can be followed to protect stored data, such as using encryption mechanisms for data at rest and in transit. Additionally, access to data should be limited only to necessary people and processes. Regular data audits and monitoring are also vital components of maintaining secure information storage.
Anonymization and pseudonymization of sensitive information
To minimize the risk of violating user privacy, personal data should be anonymized or pseudonymized. Anonymization involves deleting or altering identifying information, such as name or address, to make the data anonymous and unidentifiable. Pseudonymization is achieved by assigning unique keys to identifiers, which makes it difficult to access sensitive data.
Secure processing of payments and financial data
If your app processes users' payments or financial information, it is crucial to ensure their security. Payment processing should follow industry guidelines such as the PCI DSS standard. For mobile apps, this means securely storing financial data and monitoring transactions for irregularities or fraud attempts.

The future of mobile app security
Technology development and its impact on security - The latest technologies, such as artificial intelligence (AI) and machine learning (ML), can both enhance and weaken application security. AI and ML can help automatically detect and defend against attacks, but they can also be used by hackers. The growing number of IoT devices presents new challenges and threats to the security of mobile applications. IoT devices often communicate with mobile applications, creating new points of attack.
Security checklist for mobile app developers
Security checklist for mobile app developers
Data Access Control - Access to data must be strictly controlled and limited to only those necessary for the application to function. Secure Communication - Use encryption protocols such as HTTPS to secure communication between the application and the server. Session Management - User sessions must be secure and should automatically expire after a specified time. Source Code Protection - Monitor and protect source code against attacks such as SQL injection or Cross-Site Scripting (XSS). Minimize Permissions - application permissions should be kept to a minimum to prevent unauthorized access to user data. Updates and patches - Regular updates are essential for detecting and fixing bugs and vulnerabilities. Testing - Regular testing is an essential aspect of identifying security vulnerabilities. File and Local Data Security - Store data in a secure and encrypted manner. Develop an Incident Response Plan – Developing an Incident Response Plan will help you to respond quickly and effectively to security incidents.
Conclusions
Conclusions


















